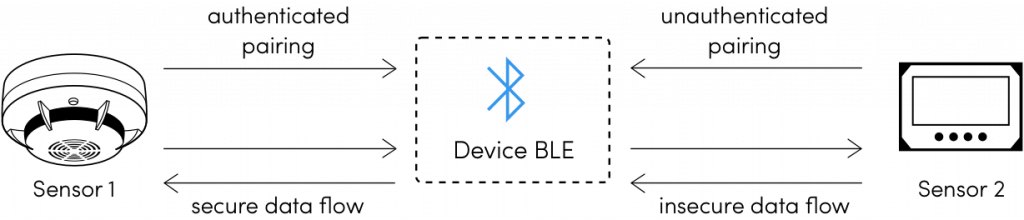
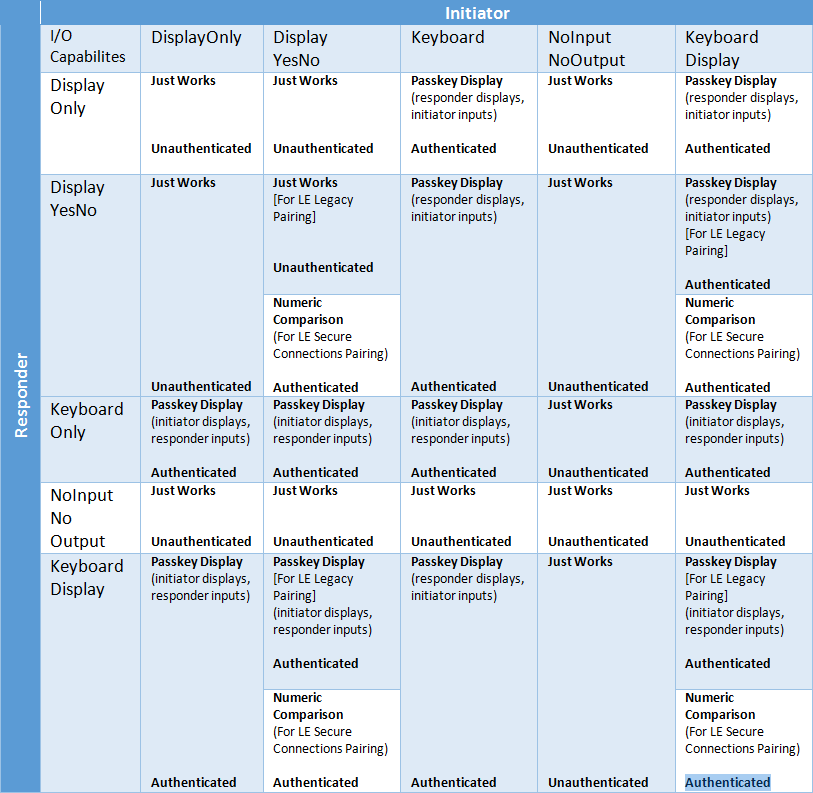
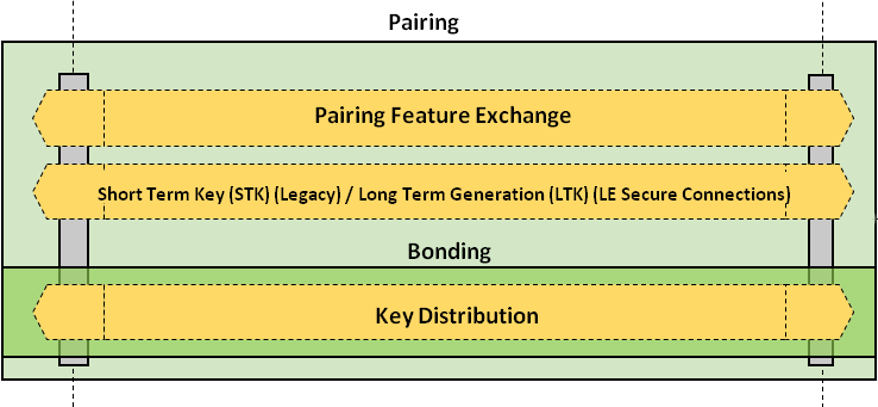
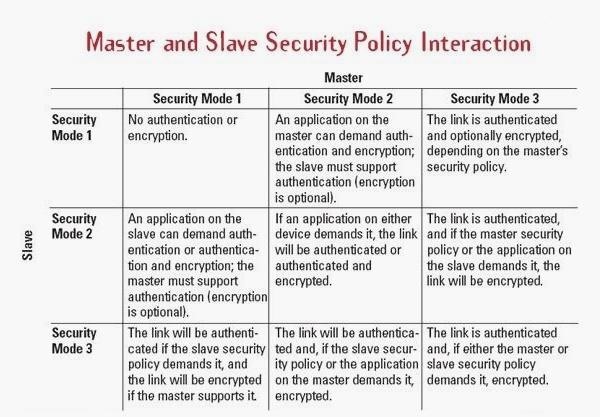
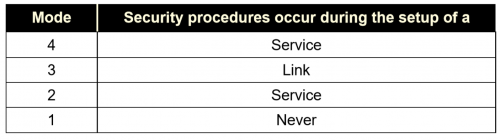
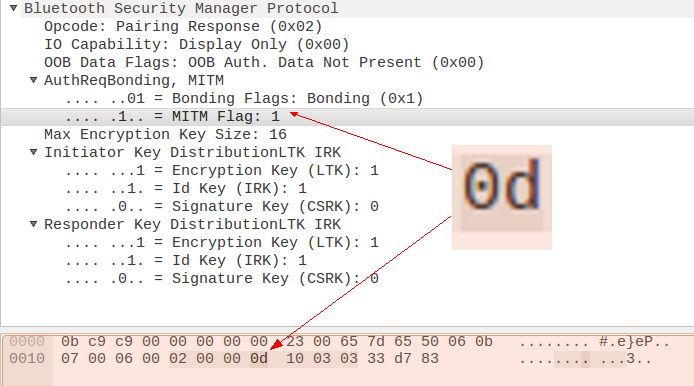
Bluetooth Pairing Part 4:Bluetooth Low EnergySecure Connections -Numeric Comparison | Bluetooth® Technology Website

GREENCYCLE Wireless Bluetooth Home Store Security Burglar Alert, Vibration and Magnet Alarm Sensors with Red Light Flash for Windows and Doors, Intelligent Magnetic Alarm, 4 Working Mode,App Control - Walmart.com
IWD2243 Wireless & Mobile Security Chapter 4 : Security in Wireless Ad Hoc Network Prepared by : Zuraidy Adnan, FITM UNISEL1. - ppt download

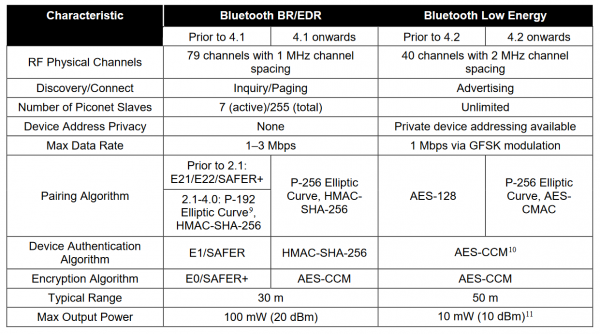
Figure 4-5 from Wireless Network Security: 802.11, Bluetooth and Handheld Devices | Semantic Scholar